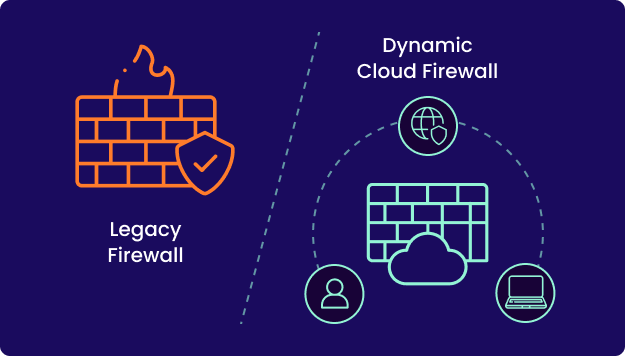
The traditional network perimeter has dissolved. Data and users are everywhere. Apps live in the cloud. Legacy firewalls can’t keep up. The Timus Dynamic Cloud Firewall delivers Zero Trust identity and role-based security from anywhere, without needing hardware or complicated configurations. It works alongside your existing firewalls as a unified, software-defined point of control for the modern workforce.
Real-time protection that adapts to your users, devices, and cloud — without the complexity.