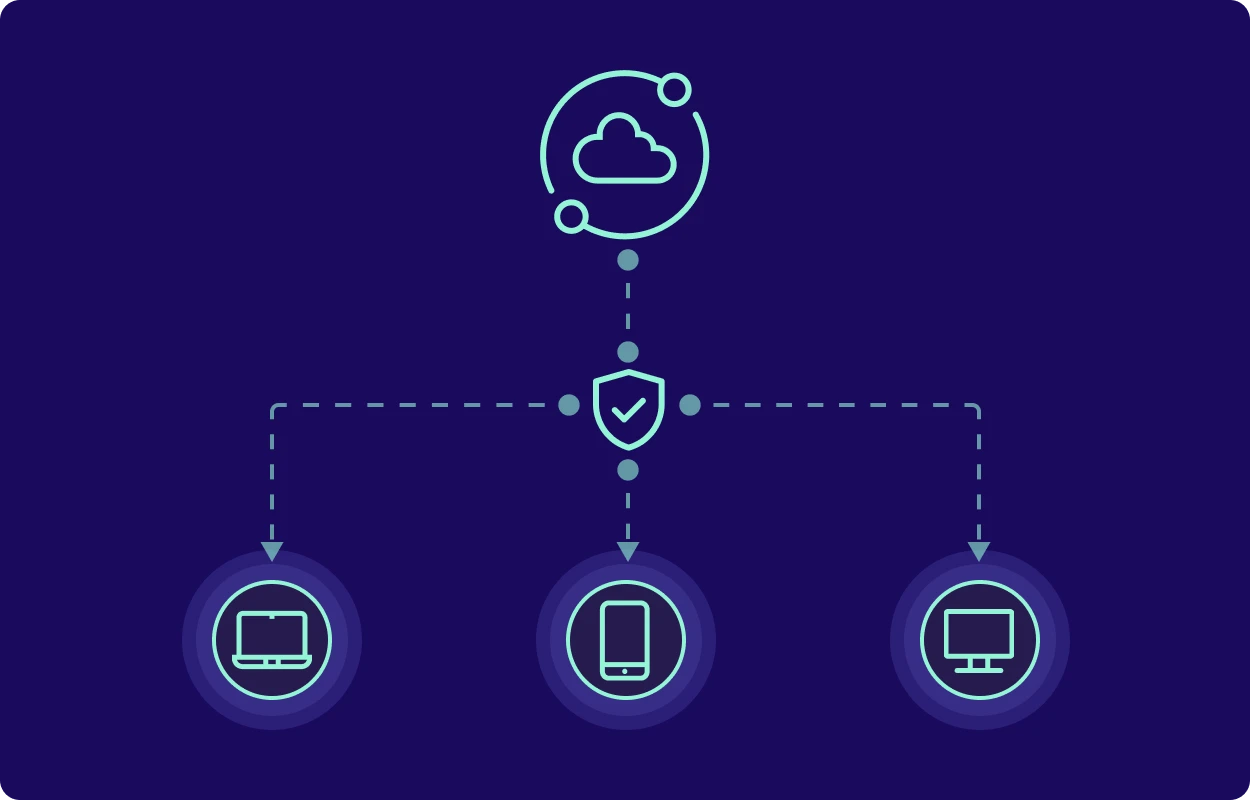
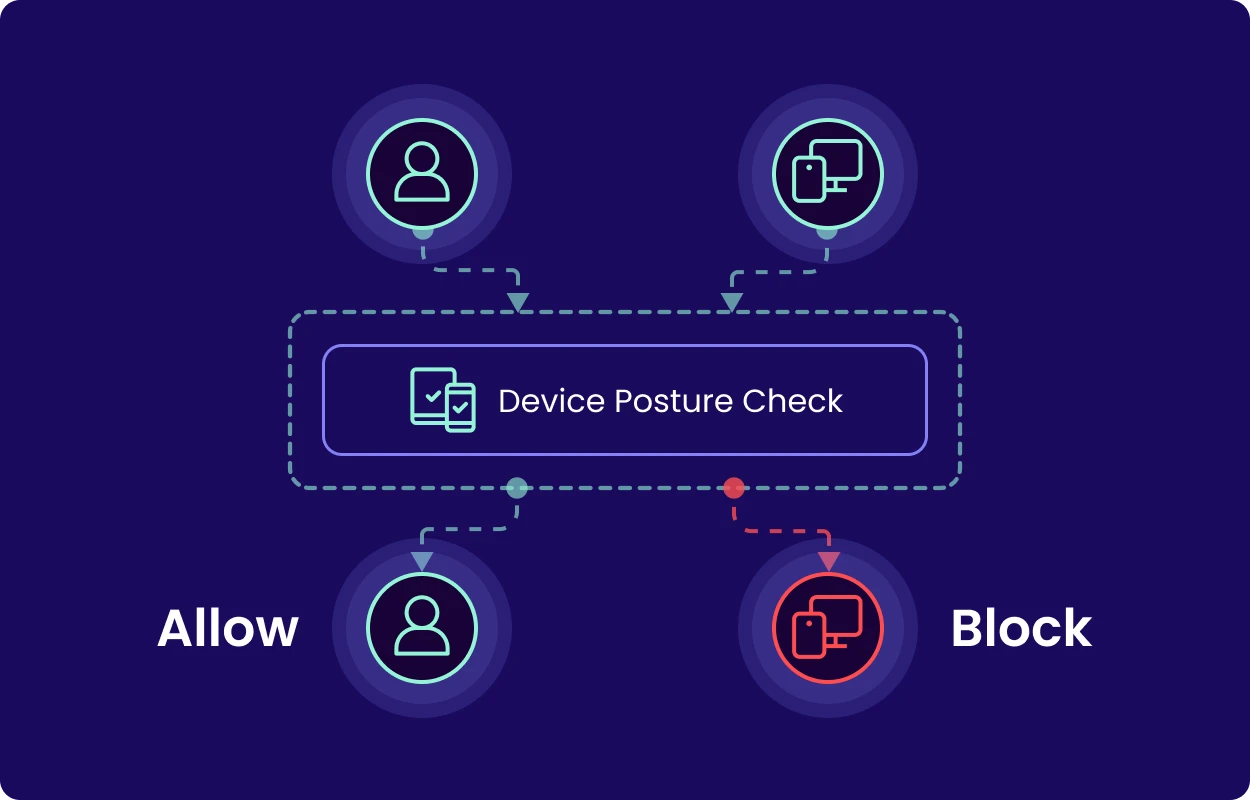
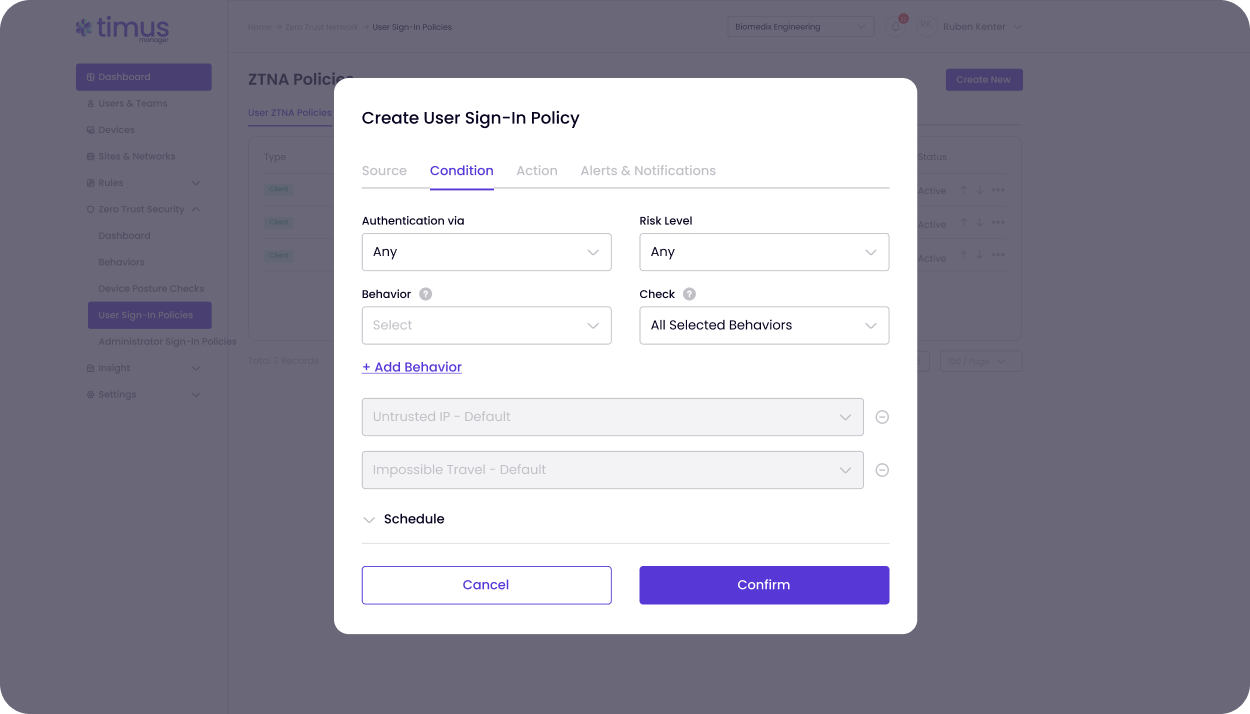
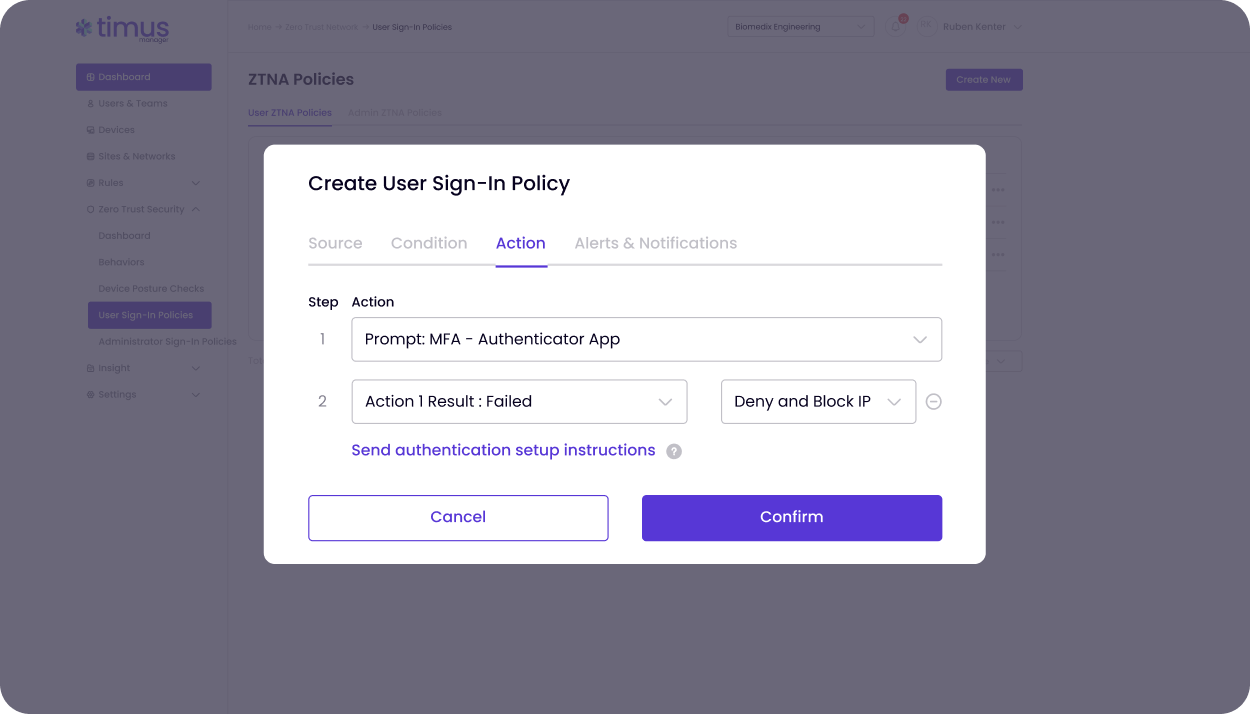
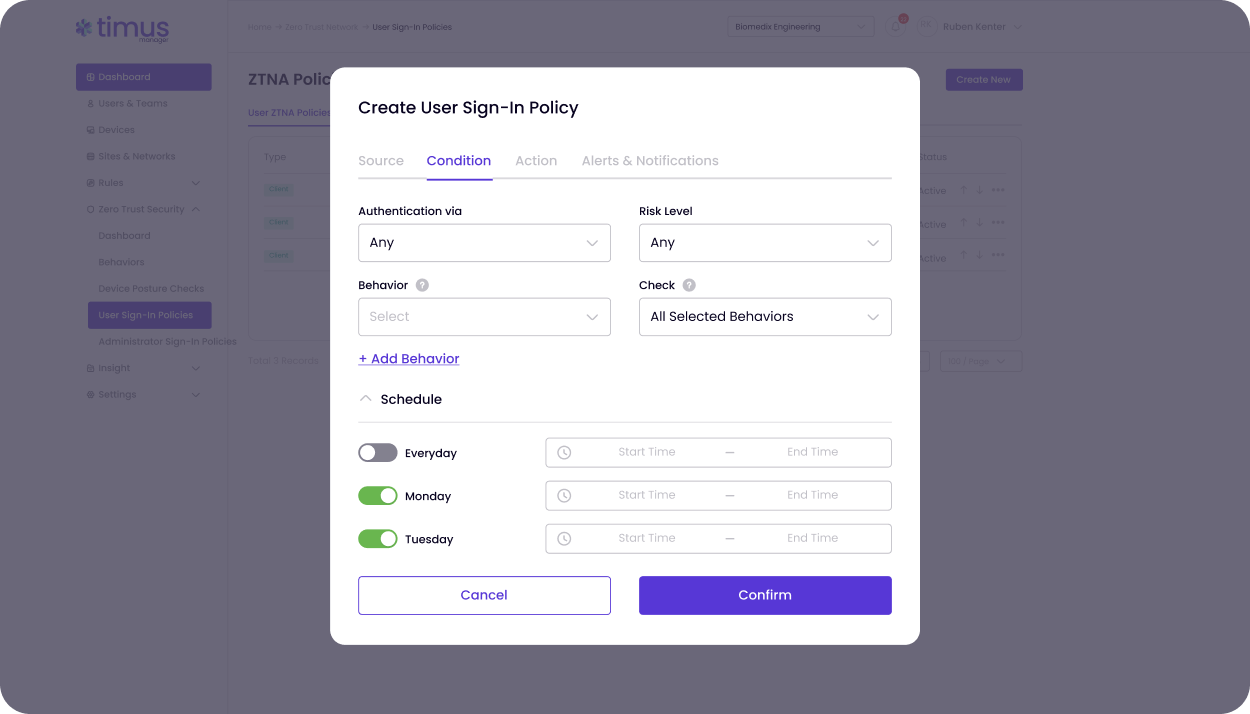
DPC reinforces Zero Trust Access by validating every device before allowing network access. Compliant devices connect seamlessly. Non-compliant ones get blocked — or limited — automatically. This is Zero Trust made practical for MSPs.
Automated posture checks integrated with leading EPPs to proactively protect your endpoints and your clients — the MSP way.