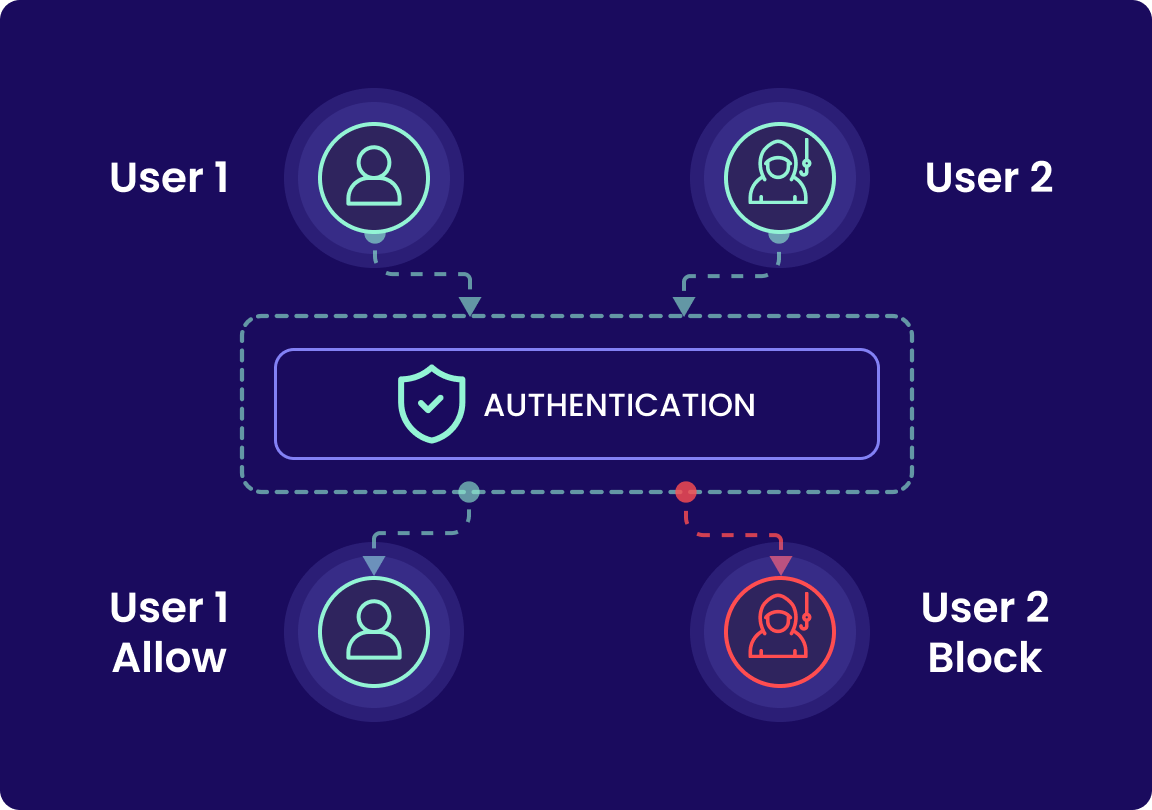
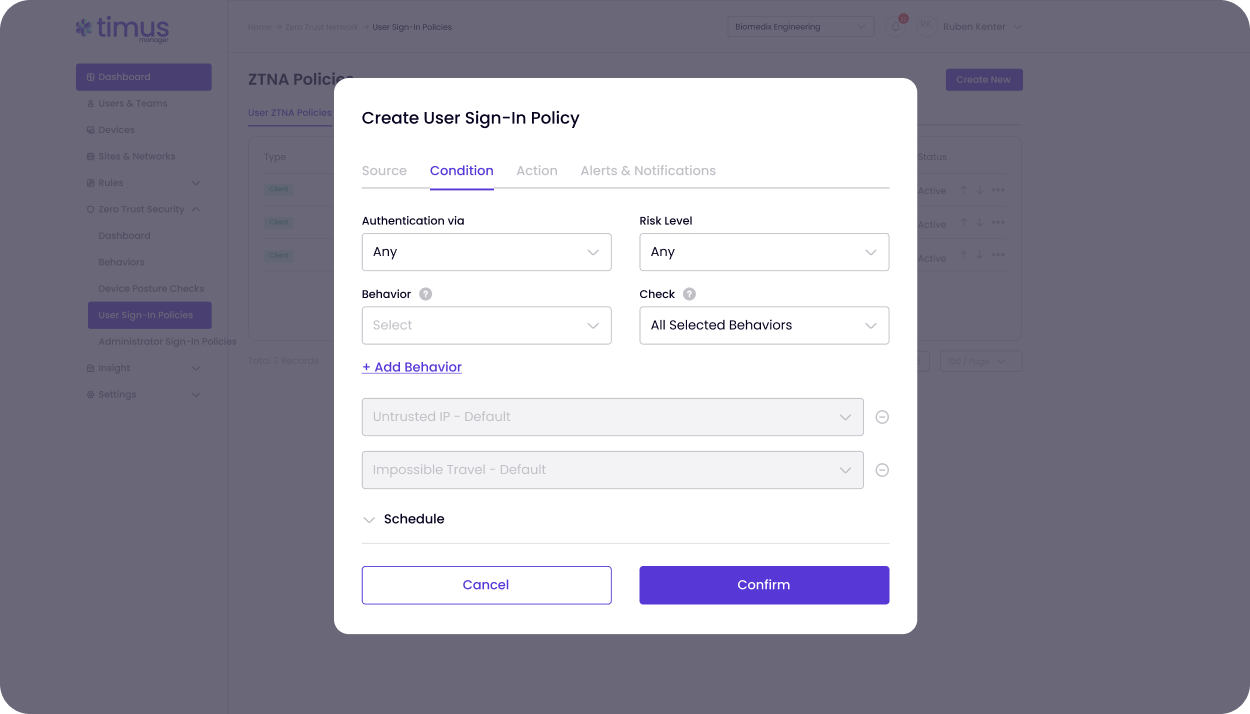
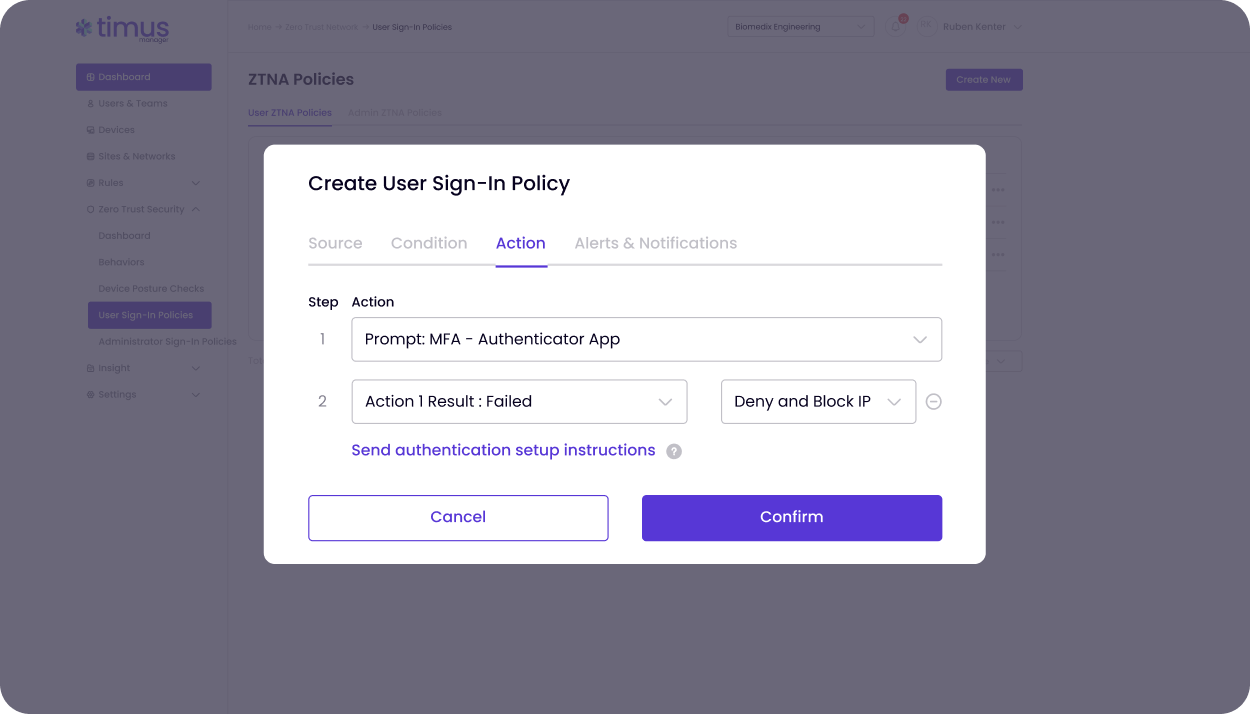
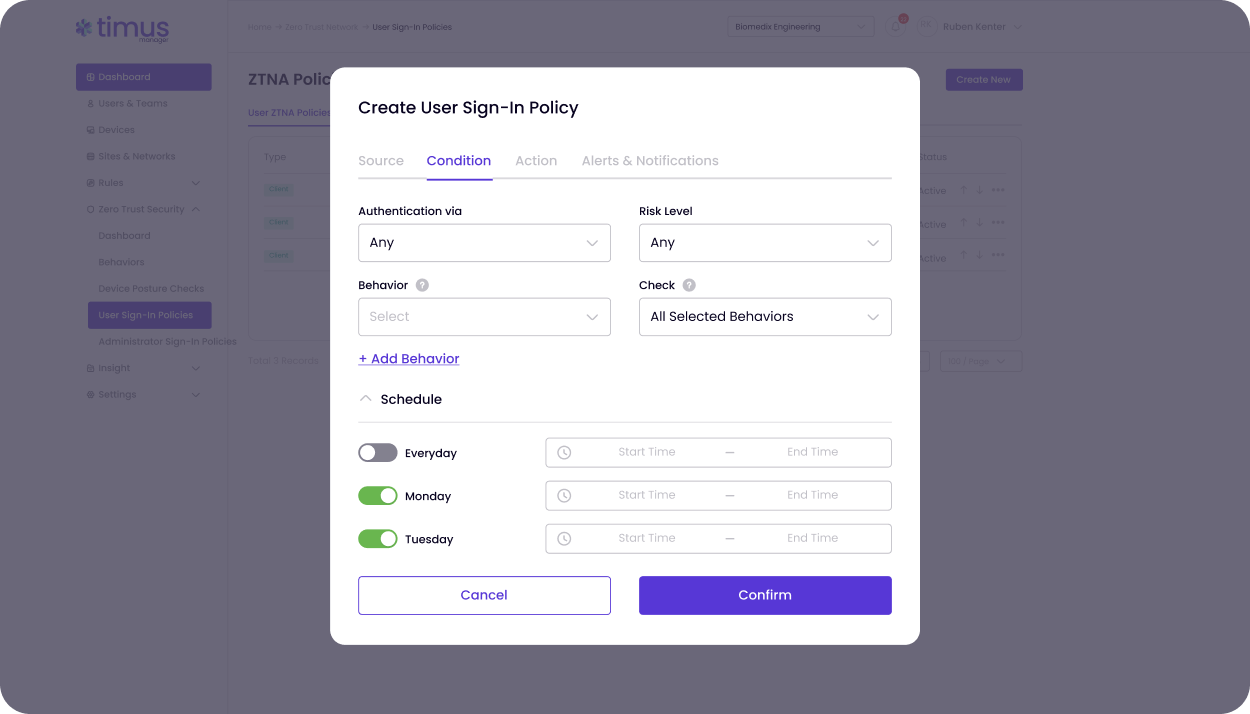
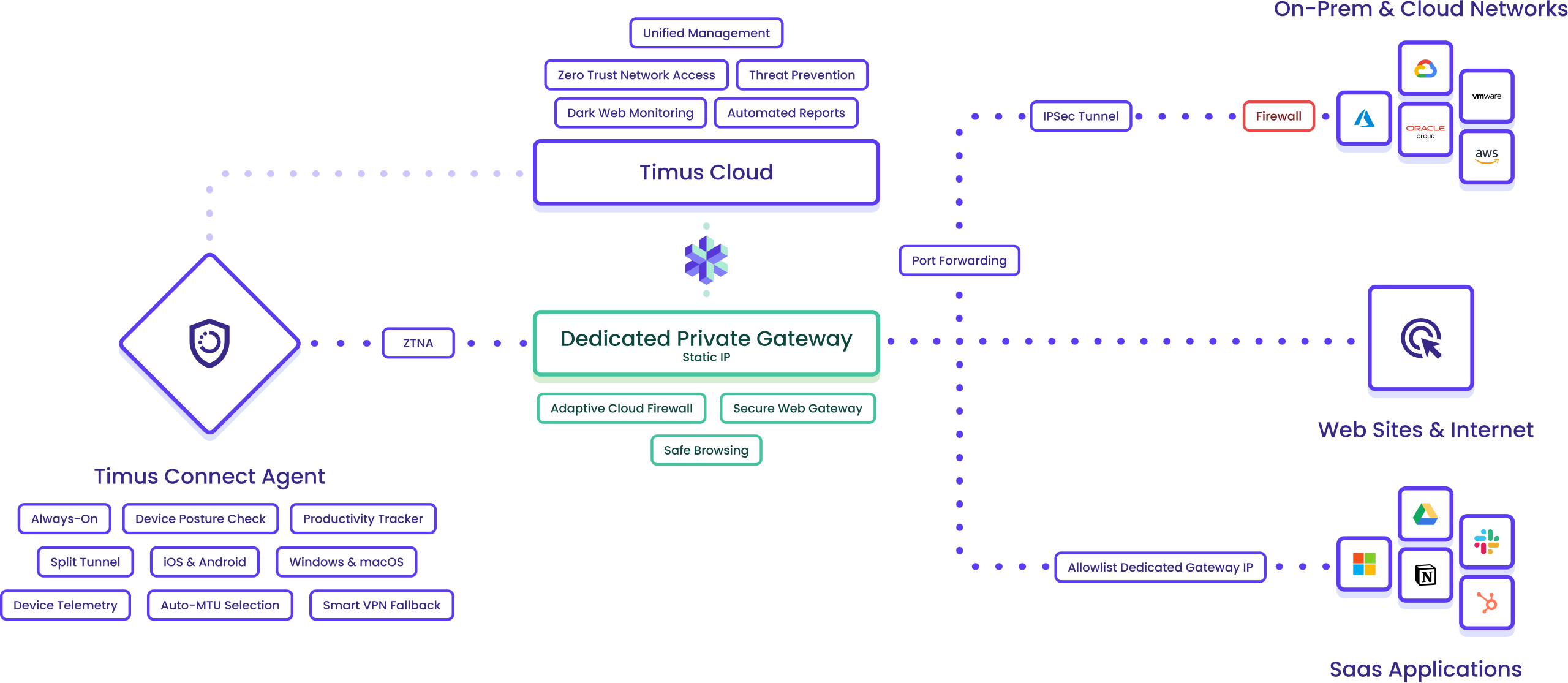
Timus ZTNA along with Secure Web Gateway gives your clients what legacy VPNs never could: simple, secure access that never gets in the way, and the ability to browse the internet without getting phished. With identity-first authentication and device posture enforcement, users stay securely connected from anywhere.
Timus SASE is designed around the three pillars that solve the biggest challenges for MSPs: seamless secure access, actionable intelligence, and total control.