Adopting a strong security strategy is crucial in the current digital environment, where cyber threats abound. The conventional castle-and-moat method, which relied on the trust of everything within the network perimeter, is becoming outdated. The zero-trust security model, however, represents a significant shift. It questions the idea of inherent trust and ensures that every user, device, and application undergo continuous verification before being granted access to sensitive resources.
This guide explores the complexities of implementing a zero-trust architecture, equipping you with the knowledge and best practices to fortify your organization’s defenses against ever-evolving cyber threats.
What is the Meaning of Zero-trust Implementation?
Zero-trust implementation refers to the process of adopting a security framework that operates on the principle of “never trust, always verify.” This approach mandates that every access request, regardless of its origin – internal or external – is subjected to stringent authentication, authorization, and continuous monitoring measures.
The fundamental principle of zero-trust is to remove the idea of a trusted network boundary, acknowledging that threats can arise from within and outside the organization. zero-trust implementation seeks to reduce the attack surface and lessen the impact of successful breaches by considering every user, device, and application as a potential threat.
Implementing Zero-trust in Five Steps
Transitioning to a zero-trust security model is a multifaceted endeavor that requires careful planning, execution, and ongoing monitoring. Here are five essential steps to guide you through the implementation process:
SASE
Secure Access Service Edge (SASE) is a cloud-native security architecture that converges networking and security functionalities into a unified, globally distributed service. Implementing SASE as part of your zero-trust strategy can provide several benefits, including:
- Integration: Ensure seamless integration with your existing network architecture, enabling secure connectivity between on-premises and cloud resources.
- Features: Leverage advanced capabilities such as micro-segmentation, patching, sandboxing, and identity and access management to enhance your security posture.
- Containment: Implement robust containment measures to limit the impact of potential breaches and minimize lateral movement within your network.
Micro-segmentation
Micro-segmentation involves dividing your network into smaller, isolated segments based on specific security requirements. By implementing micro-segmentation, you can define granular access controls, allowing users, applications, and devices to access only the resources they require to perform their designated tasks.
This approach significantly reduces the attack surface and limits the potential for lateral movement within your network, effectively containing threats and minimizing the risk of widespread data breaches.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a foundational element of zero-trust security. It mandates that users furnish two or more authentication factors, including something they know (e.g., a password), something they possess (e.g., a mobile device or token), and something they are (e.g., biometric data like fingerprints or facial recognition).
By implementing MFA, you can significantly enhance the security of your systems by ensuring that only authorized users with valid credentials can gain access, reducing the risk of unauthorized access and account compromises.
Principle of Least Privilege (PoLP)
The principle of least privilege (PoLP) is a fundamental concept in zero-trust security. It dictates that users, applications, and devices should be granted only the minimum level of access required to perform their specific tasks or functions.
By adhering to the PoLP, you can minimize the potential impact of successful breaches and limit the ability of malicious actors to move laterally within your network, effectively containing threats and reducing the risk of data exfiltration or system compromise.
Endpoint Device Protection
In a zero-trust environment, endpoint devices are considered potential entry points for threats. As such, it is crucial to implement robust endpoint security measures, including device validation, encryption, and continuous monitoring.
Ensure that all endpoint devices meet your organization’s security requirements before granting them access to your network resources. This may involve device enrollment, software and firmware updates, and the deployment of endpoint protection solutions.
Challenges in Implementing Zero-Trust
While the benefits of a zero-trust security model are undeniable, its implementation can be demanding on resources and organizations must be prepared to address this.
- Complex Infrastructure: Modern organizations often have intricate infrastructure consisting of various components, such as servers, proxies, databases, applications, and cloud services. Securing each segment of this complex environment while catering to hybrid architectures can be a daunting task.
- Operationalizing zero-trust: Implementing zero-trust may require the integration of multiple tools and solutions, including zero-trust Network Access (ZTNA), Secure Access Service Edge (SASE), micro-segmentation tools, multi-factor authentication (MFA), and device approval solutions. Ensuring seamless interoperability and consistent policy enforcement across these diverse components can be challenging, especially in large organizations with heterogeneous environments.
- Mindset Adjustment: Adopting a zero-trust model often necessitates a cultural shift within the organization. Stakeholder buy-in, effective training, and comprehensive planning are crucial to ensure a smooth transition and long-term success.
- Cost and Effort: Implementing zero-trust can be resource-intensive, requiring significant investments in time, human capital, and financial resources. Defining access controls, network segmentation, and continuous monitoring mechanisms demands careful planning and collaboration across various teams.
How Do You Get Zero-trust Security?
Achieving a strong zero-trust security posture requires a systematic approach that includes several essential elements:
- Identify Critical Assets: Begin by identifying your organization’s most valuable digital assets, including sensitive data, critical applications, physical assets, and corporate services. This “protect surface” will serve as the foundation for your zero-trust implementation.
- Understand Application Interactions: Understand how your applications interact with one another and the dependencies they have on various resources, such as databases and third-party services. This knowledge will inform your access control and segmentation strategies.
- Architect the zero-trust Framework: Based on your identified protect surface (also known as Data, Assets, Applications, Services (DaaS)) and application interactions, design a zero-trust architecture that incorporates security measures like micro-segmentation, identity and access management, and continuous monitoring.
- Develop zero-trust Policies: Use the Kipling Method (who, what, when, where, why, and how) to define granular access policies that govern user, device, and application interactions within your zero-trust environment.
- Continuous Monitoring and Adaptation: Implement robust monitoring mechanisms to track and analyze network activity, user behavior, and potential threats. Leverage this data to continuously refine and adapt your zero-trust policies, ensuring an ever-evolving and resilient security posture.
What is an Example of Zero-Trust Security?
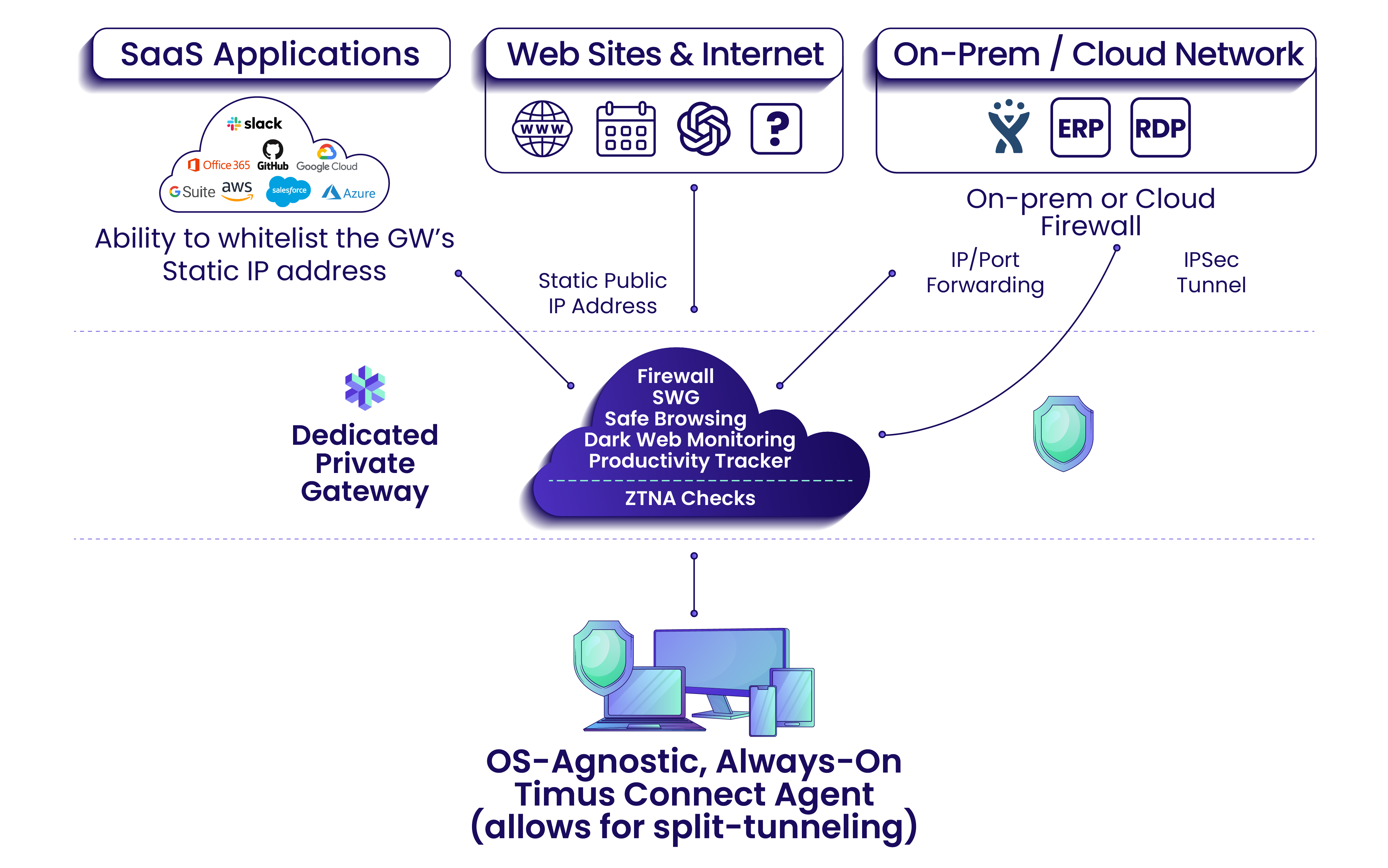
Timus provides an acclaimed Zero Trust Network Access (ZTNA) solution that employs a comprehensive behavioral context checklist to verify users before granting access. This includes identity-based verification, Adaptive MFA, and intelligent threat detection through an adaptive cloud firewall. By eliminating the need for VPNs, Timus ZTNA offers continuously secure connectivity.
Core Principles of ZTNA
- Based on the “never trust, always verify” principle
- Access is granted granularly on the least privilege principle
- Ensures secure, always-on connectivity for remote users and those accessing SaaS apps on company devices
Advantages of ZTNA Over Traditional VPNs
- Protects against ransomware and other cyber threats
- Mitigates human error as a weakness in cybersecurity defenses
- Prevents access to company resources from unwanted third parties
Disadvantages of Traditional VPNs
Timus ZTNA addresses several drawbacks of traditional VPNs, including:
- Clunkiness of traditional VPNs
- Lack of always-on connectivity
- Vulnerability to social engineering and phishing attacks
- Potential lateral movement within the network via stolen VPN credentials
Timus ZTNA offers granular access to company resources with secure, always-on connectivity through a lightweight OS-agnostic agent.
Which one is the best security practice for Zero-Trust?
While there is no one-size-fits-all approach to zero-trust security, several best practices can guide organizations in their implementation efforts:
- Start Small: Begin by addressing specific pain points or use cases within your ecosystem, such as exposed attack surfaces or over privileged access. This approach allows you to build a solid foundation and gain valuable experience before tackling more complex challenges.
- Re-evaluate Legacy Investments: Critically assess whether your existing legacy tools and technologies align with your current business objectives, meet security requirements, and effectively address the challenges posed by cloud adoption, mobility, and the Internet of Things (IoT).
- Stakeholder Engagement: Engage key stakeholders across your organization to understand their drivers, concerns, and potential legal or compliance risks. Socialize your initial use cases to secure early buy-in and support.
- Leverage Expertise: Recognize that your team may not possess the necessary expertise to execute a zero-trust transformation independently. Seek expert assistance from proven professional services and managed security service providers to accelerate your journey.
- Embrace Mutual Delivery Plans: Collaborate with your vendor partners to develop mutual delivery plans (MDPs) that outline a clear roadmap, individual steps, and shared responsibilities for achieving your zero-trust goals.
- Continuous Improvement: Treat zero-trust as an ongoing journey, continuously monitoring and refining your policies, processes, and technologies to adapt to evolving threats and business requirements.
FAQ
Implementing zero-trust can be demanding, particularly for organizations with complex infrastructures and legacy systems. However, by adopting a phased approach, engaging stakeholders, and leveraging expert guidance, you can mitigate the challenges, and the benefits of enhanced security and reduced risk can outweigh the initial effort.
Firewalls can still play a role in certain implementations. However, zero-trust extends beyond firewalls by incorporating additional layers of security, such as micro-segmentation, identity and access management, and continuous monitoring.
The time required to implement zero-trust varies depending on your organization’s complexity, the solution chosen, and the scope of your implementation. Larger organizations with intricate infrastructures may need more time to document processes, define access controls, and segment their networks. However, investing time upfront to assess and plan for your critical assets can streamline the process. By embracing the zero-trust security model, organizations can fortify their defenses against modern cyber threats, protect their sensitive data and critical assets, and foster a culture of continuous vigilance and trust-based access. While the journey may present challenges, enhanced security, reduced risk, and a resilient security posture make the effort worthwhile in today’s ever-evolving threat landscape.