Fortify Your Network with Automated, Granular Device Posture Checks
Seamlessly integrated with leading EPPs (Microsoft Defender for Endpoint, Bitdefender, and SentinelOne) for proactive and continuous protection
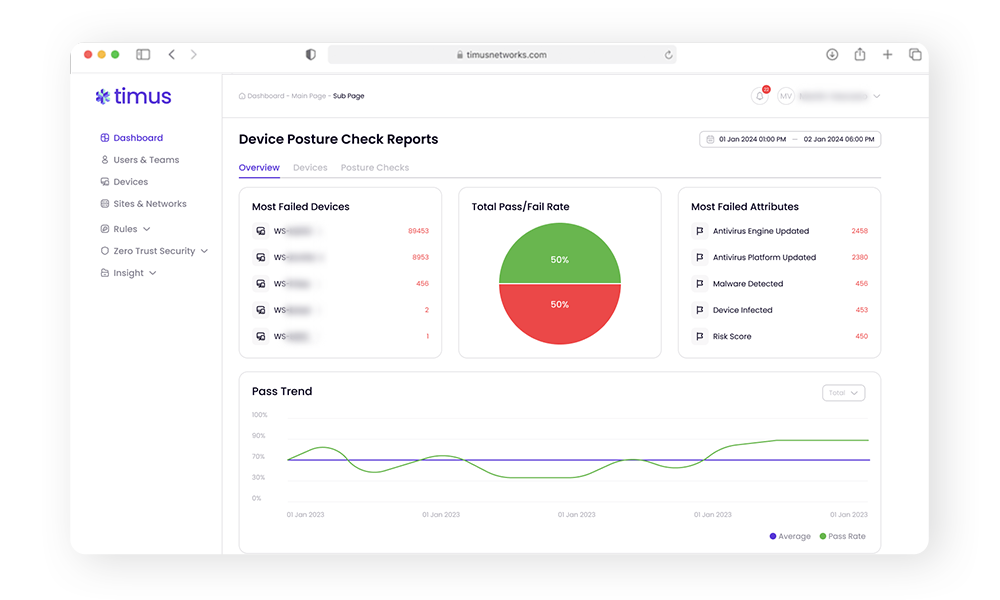
Seamlessly integrated with leading EPPs (Microsoft Defender for Endpoint, Bitdefender, and SentinelOne) for proactive and continuous protection


Benefit from real-time device posture evaluation, ensuring proactive and continuous protection against threats.

EPP integrations allow for combined endpoint and network security management, streamlining security workflows.

Increase IT efficiency and cost savings through automated device management, enhanced vulnerability identification, and remediation.
1.png)
Take command with granular control over device access, leveraging comprehensive security posture insights.
Device Posture Check (DPC) proactively identifies non-compliant devices, thwarting malware, ransomware, and APTs. It enforces security standards, minimizing gaps, reducing the attack surface, and enhancing network hygiene.
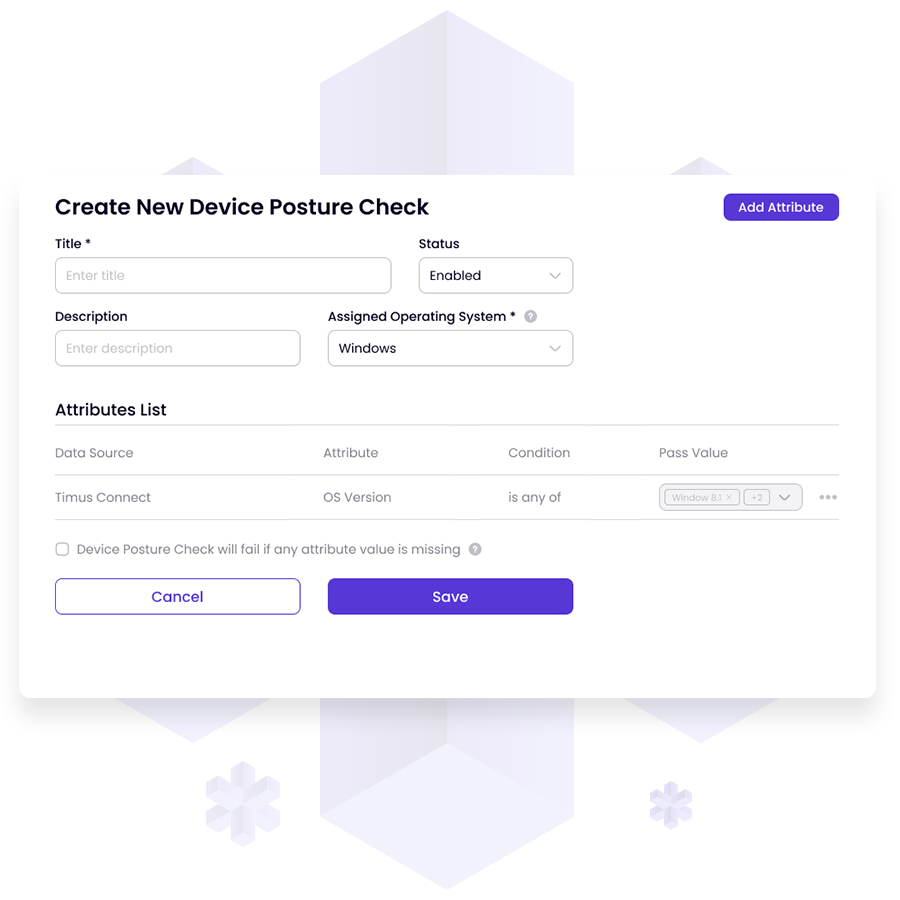
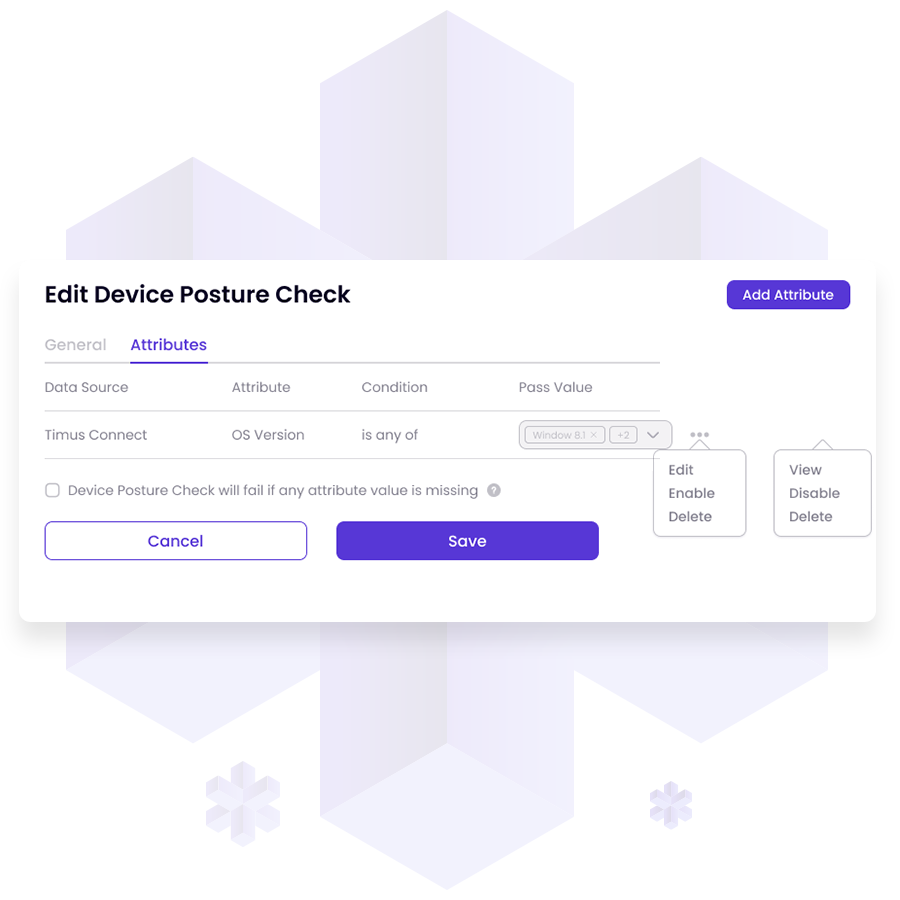
DPC enables administrators to set precise access rules based on device status. Full access is permitted to compliant devices, partially compliant devices face limitations, while non-compliant devices are denied access. DPC offers enhanced visibility, displaying endpoint details and security status, aiding decision-making and prioritizing remediation efforts.
Continuous verification of device security aligns with Zero Trust principles, and only grants access to trusted devices. This reduces reliance on boundary protection, minimizing risks from sophisticated attacks. DPC ensures robust protection against unauthorized access attempts, aligning seamlessly with modern security paradigms.
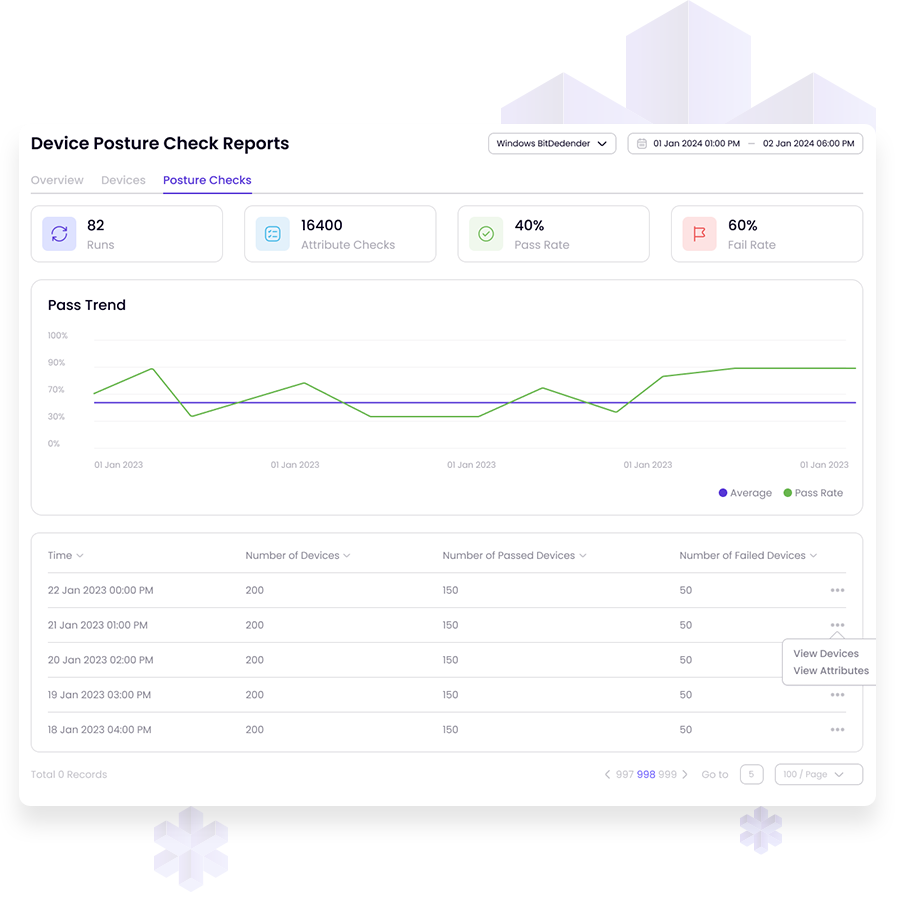
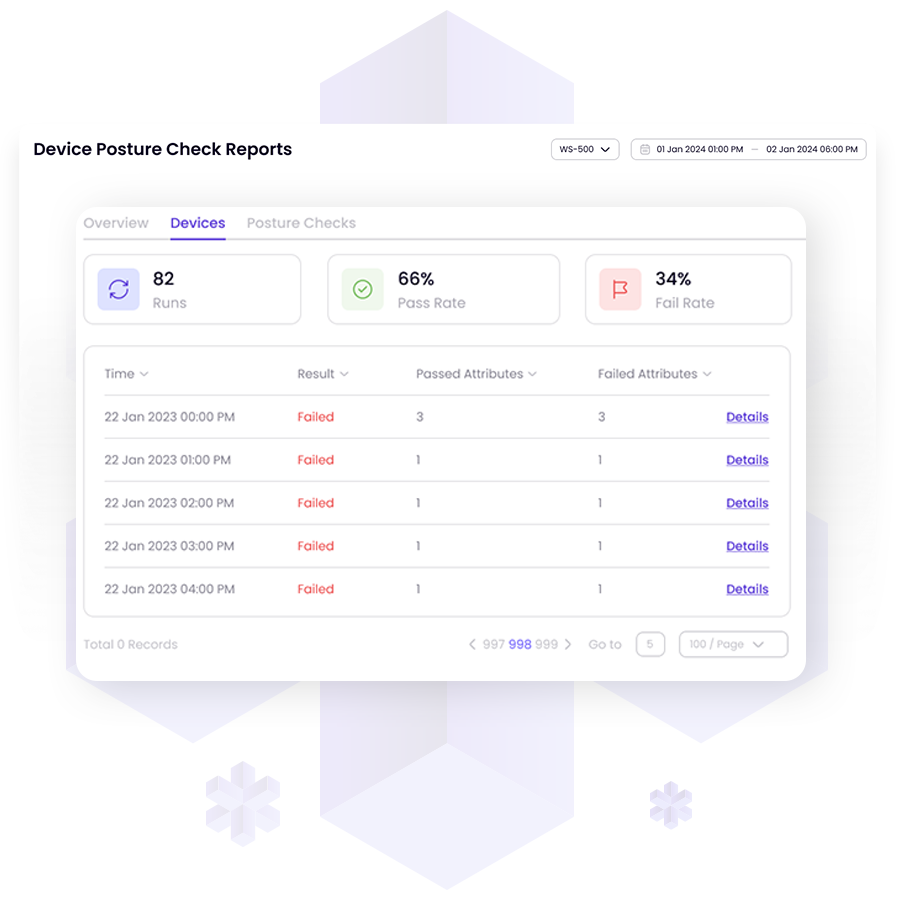
DPC streamlines security processes, automating assessments and remediation tasks for IT teams. Rapid identification and resolution of device vulnerabilities enhance efficiency, minimizing threat exposure and reducing costs.